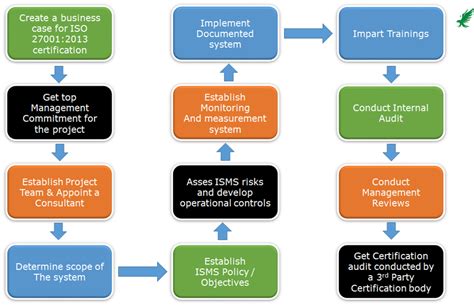
An information security management system (ISMS) is a framework of policies and controls that manage security and risks systematically and across your entire company or organisation.
The framework for ISMS is usually focused on ISO 27001 a set of specifications detailing how to create, manage, and implement ISMS policies and controls. The ISO doesn't mandate specific actions; instead, it provides a guideline on developing appropriate ISMS strategies and compliance with a host of laws like the EU General Data Protection Regulation (GDPR).